Introduction
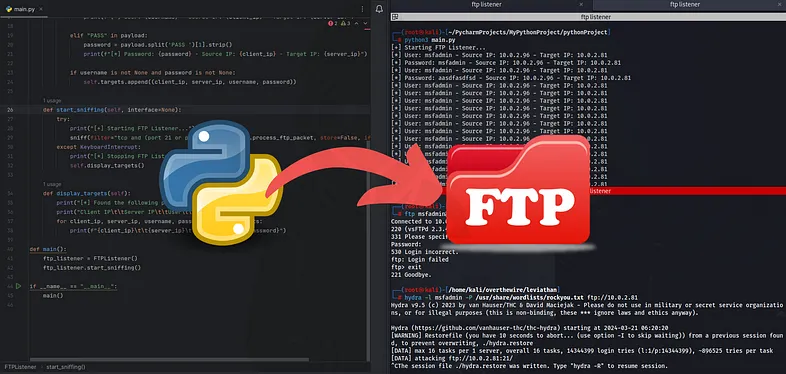
As cyber threats continue to evolve, network security remains a top priority. Monitoring specific protocols like FTP (File Transfer Protocol) can reveal vulnerabilities that might otherwise go unnoticed. In this article, we’ll guide you through building an FTP listener using Scapy, a powerful Python library designed for network traffic analysis.
Learning Objectives
- Gain an understanding of Scapy and its use in network security.
- Learn how to monitor FTP traffic to detect potential security risks.
- Understand the practical application of an FTP listener.
Understanding FTP
FTP is a widely used protocol for transferring files over a network. However, because it transmits data, including login credentials, in plaintext, it is susceptible to interception and exploitation by malicious actors.
Project Purpose
The aim of this project is to create a tool that listens to FTP traffic and captures unencrypted credentials. This allows for the identification of potential security flaws, providing insights into the need for more secure protocols.
Let’s Write Some Code
from scapy.all import sniff, TCP, Raw, IP
This import statement pulls in essential functions from Scapy, which we’ll use to capture and analyze FTP packets on the network.
Conclusion
This brief overview covered the essential steps to develop an FTP listener using Scapy. Such tools are vital for identifying weaknesses in network security. Always ensure that your use of network monitoring tools aligns with ethical guidelines and legal requirements.
For a detailed walkthrough and complete code, check out the full article: Creating an FTP Listener with Scapy for Network Security







