Introduction
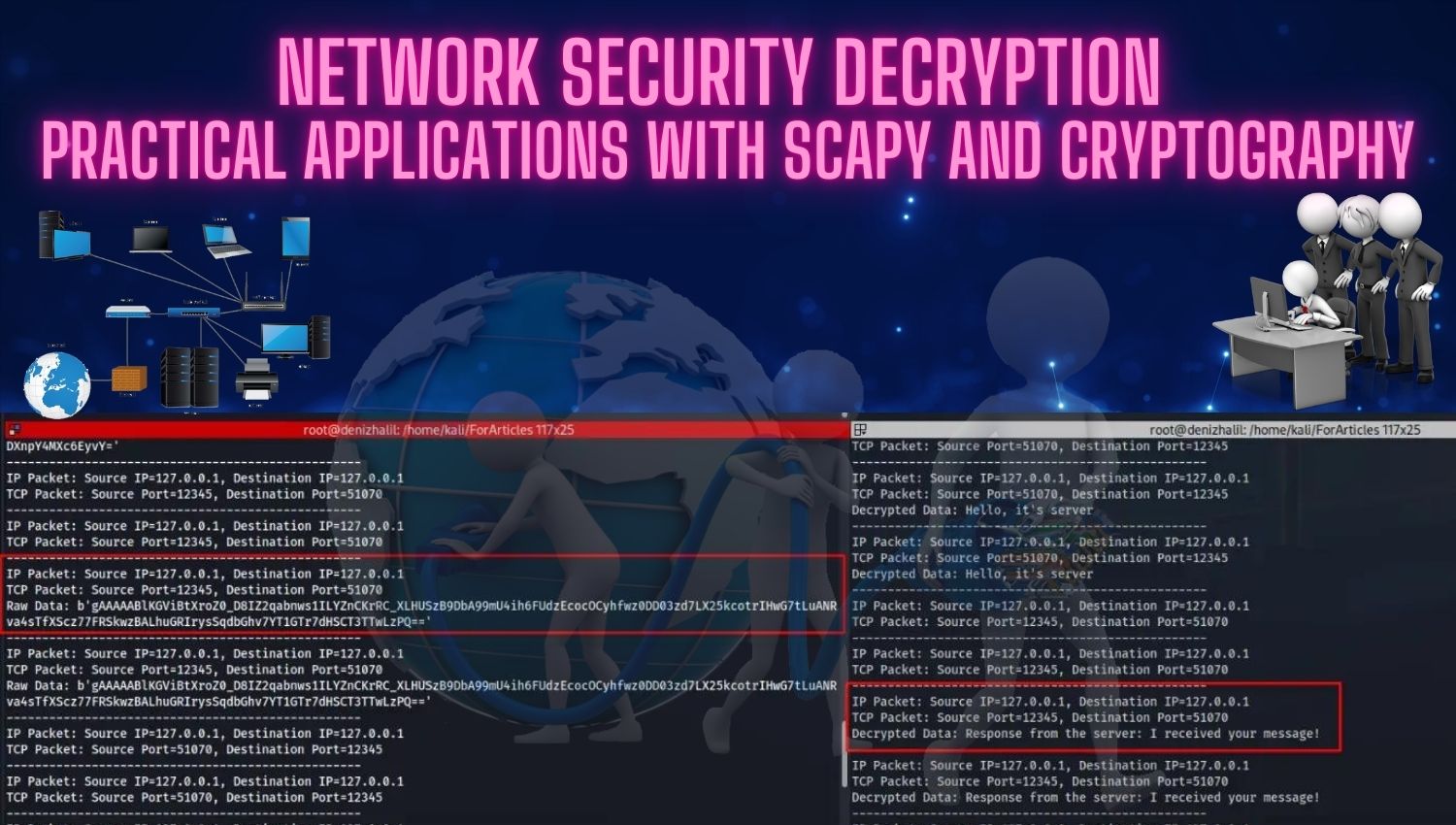
In today’s digital landscape, protecting sensitive data during network transmission is critical. Encryption plays a vital role in ensuring that data remains secure, preventing unauthorized access. However, in certain scenarios, such as security analysis or network troubleshooting, decrypting and examining encrypted traffic becomes necessary. This article explores how Python, along with the Scapy library, can be utilized to capture and analyze encrypted network traffic, addressing both scenarios where the encryption key is available and where it is not.
Learning Objectives
- Gain an understanding of network encryption and its significance in maintaining data security.
- Learn how to use Python and Scapy to intercept and analyze encrypted network traffic.
- Discover how to handle network traffic analysis in situations where the encryption key is either accessible or not, along with the associated challenges.
Network Encryption Methods
Encryption involves converting data into a secure format, ensuring only authorized users can access it. The two primary methods of encryption are symmetric, where the same key is used for both encryption and decryption, and asymmetric, which involves a pair of keys—one for encryption and another for decryption. Grasping these concepts is essential before delving into decryption and traffic analysis.
Purpose of This Project
This project aims to showcase how encrypted network traffic can be intercepted and analyzed using Python and Scapy. Whether the encryption key is available or not, the project will demonstrate how to either decrypt the data or analyze the metadata to extract critical information.
Conclusion
Understanding how to decrypt and analyze encrypted network traffic is crucial for network security professionals. This article outlines the challenges and techniques involved in working with encrypted data, whether the encryption key is accessible or not. Python and Scapy offer powerful capabilities for both decrypting network traffic and extracting metadata for analysis.
For a deeper dive into the methods and code examples discussed in this article, check out the full guide here





